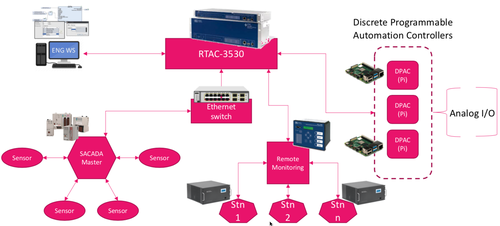
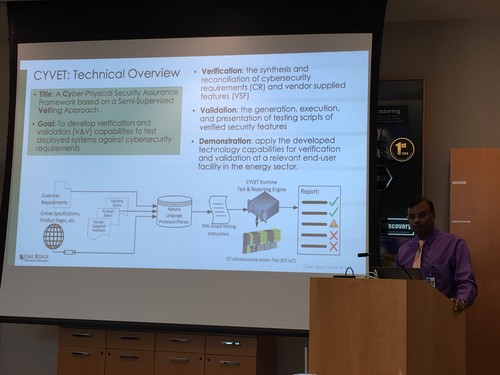
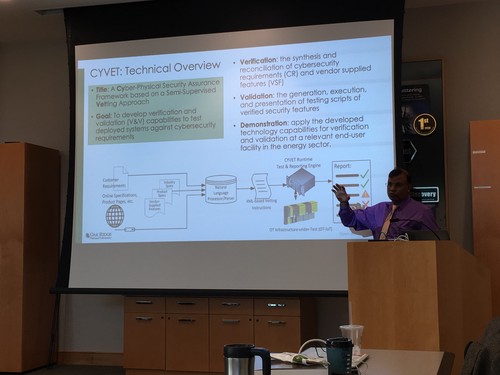
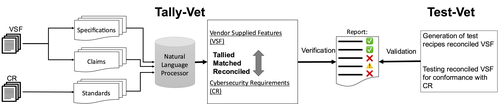
CYVET
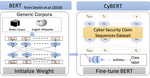
Our new Cyber-Physical Security Assurance Framework based on Semi-Supervised Vetting applies the latest AI/ML and NLP technologies on hardware testbeds to advance the resilience of critical cyber-physical assets including electric grids and gas pipelines.
Overview
Organization
- Sponsor: US Department of Energy (DOE)
- Office: Cybersecurity, Energy Security, and Emergency Response (CESER)
- Program: Cybersecurity for Energy Delivery Systems (CEDS)
- Award: CESER
- Prime: Oak Ridge National Laboratory (ORNL)
- Subcontract: University of Nebraska-Lincoln (UNL)
- Period: 2019-2023
Gallery
Related Publications
OSTI.gov: https://www.osti.gov/servlets/purl/1661247
Additional Background
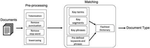
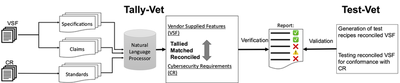
The cybersecurity auditing for Operation Technology (OT) is critical and has been largely missing from the cybersecurity research, especially in the energy sector. CYVET is a novel “cybersecurity vetting” approach (CYVET) to the problem of verification and validation of cybersecurity in complex cyber-physical installations underlying modern energy grid systems.
In Information Technology (IT), cybersecurity auditing is a widespread practice to ensure privacy, security, and trust. However, for the field of Operation Technology (OT) as used in electric energy systems, this is a relatively novel concept. In fact, OT itself only recently began to embrace IT principles, with the push for automation and centralized control driving this development. OT operators are simply not yet used to the idea of cybersecurity. To ameliorate the gap, product vendors for field devices are advancing the field by incorporating more and more security features into their products. However, customers are often either unaware of them, or do not use them, or cannot use them because of unsatisfied device ecosystem dependencies. There is thus a disconnect between what is offered, what is possible post-deployment, and what the customer expects.
There is a vast lack of cybersecurity oversight and insight, from a certification and a customer perspective alike, for OT systems in the energy sector. With new features constantly being added to new and existing products, customers are predominantly unaware what their purchased solutions are capable of, or not capable of. They often do not know if their current systems meet their own cybersecurity requirements as well as industry standards. Many of these facets not only indirectly depend on device capabilities, but also on device deployment decisions – Does a newly added feature work in an existing context? Can it be used as envisioned? Does it interfere with other cybersecurity requirements? Does it produce side effects that may interfere with other requirements?
Hence, what is needed is a security vetting system designed to provide insight into deployed systems, the match of capabilities to requirements, adherence to certification requirements, and so forth. There are few systems currently available that provide these energy grid security capabilities. OT systems are increasingly cyber-enabled, increasingly complex, and increasingly interdependent. This rapidly accelerating trend poses a clear risk for asset owners to lose confidence and for cybersecurity risk to go undiscovered until exploited by malicious parties.